
|
|

|

|

|

|

|

|

|
|

|

|

|

|

|

|

|
|
|
|
|
|
|

|

|

|

|
|
|

|
 |
|
|
|
|
Mailing List
|
|
By Joining the mailing list you will be notified of site updates.
|
|
Show Your Support For
This Site By Donating:
|
|
|
|
|

|
|
|
|
Audience: Newbies
Last Updated: 10/17/04 7:46 AM
**All times are EST**
|
|

NAT Firewalls
By Erik Rodriguez
Tags: NAT, NAT configuration, Address Translation, Source NAT, Destination NAT, Full NAT, IP maquerading, SNAT, DNAT, MIP, DIP
This article provides information on NAT. Examples of its operation are provided and explained.
Introduction
Network Address Translation (NAT) is commonly use on firewalls and routers. NAT plays a huge role in translating private IP addresses to public IP addresses. It is also commonly referred to as IP masquerading.
- Connects a multiple devices through one or more public IP addresses
- Increases security
- Saves public IP addresses
NAT Operation
NAT is commonly used to translate private networks to public networks like the Internet. See the following you are not familiar with public and private IP addresses. NAT can be used both internally and externally. We used to seeing NAT on consumer aimed firewalls/routers like those from Linksys, D-Link, and others. They are commonly used to share your Internet connection with multiple computers in a home.
When a single address is used for Internet access, all computers attached to the NAT firewall use a different port to communicate with the devices outside the network. This increases security as there is only one entry point into the network from the Internet. Think of this as having a building with only 1 door to guard. It is much easier to guard just 1 door than say 25 doors.
NAT was designed and brought into production as a way to save public IP addresses. ISPs and network providers assume NAT will be used with your network, and often require justification for additional IP address per guidelines established by a higher power (ARIN). The following diagram shows a basic firewall running NAT:
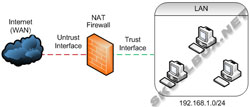
Simple NAT Firewall
|
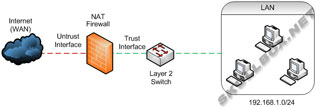
Simple NAT Firewall with Layer 2 Switch
|
click to enlarge
The second diagram takes the design 1 step further. Most firewalls have 4 ports or less. If more than 4 devices need access, they will need to aggregate at a switch that connects the a firewall. This concept gets more complicated when large networks need to operate with multiple VLANs.
Let's Use NAT for Everything!
There are some instances where NAT simply will not work. In data center enivironments, servers often connect directly to the Internet using public IP addresses that routed through a core network using BGP and other exterior routing protocols. Some software specifically requires a public IP address(es) and is NOT supported in NAT mode. Specifically speaking, cPanel will not work with NAT.
NAT vs. Route
Many firewalls provide the option to route or NAT traffic between VLANs (zones). While this can be confusing, the following examples illustrate the difference in traffic flow using each type.
Contact Us
NOTE: this form DOES NOT e-mail this article, it sends feedback to the author.
|
|
|
|
|
|
